Of all the cyber risks a business will face, phishing (the act of social engineering through malicious emails) has to be one of the greatest. If you go looking for information about how to defend yourself or your organisation, there’s no shortage of good information on the Internet, but what if you’re a sole trader, or you only employ a couple of people? Suddenly there’s a lot less guidance, which doesn’t help when you’re now in the position of having to both be phish aware, and know what to do to defend yourself.
Phishing fact and fiction
Here are six fictions that some small business owners believe when it comes to phishing. The reality isn’t quite as safe as you may imagine!
Fiction: My company is so small, nobody would target me…
Fact: Your company may be small, and nobody may target you directly, but if your email address is out on the Internet (by choice or unintentionally) someone will try to phish you.
Fiction: My staff or I would never fall for a phishing email…
Fact: The days of phishing emails just being Nigerian princes with millions of dollars to go away are long gone. Modern phishing attacks can be sophisticated, well crafted, and can even spoof your company’s email address in order to lure you into getting phished. Furthermore, even the most suspicious emails, delivered to the right person at just the right time when they’re not paying attention can get you caught.
Fiction: My email provider / antivirus will protect me…
Fact: Technology can do a lot to help reduce the risk of phishing, but it’s not a guaranteed solution. While an infected attachment may get caught by your antivirus, if the document links to content on the internet or exploits a vulnerability in your system, it won’t help. Likewise by the time a website is declared as dangerous by your browser, the attackers will have moved on. Finally, while your email provider may be able to block some suspicious emails, the attacker may not immediately make the link dangerous, only doing so after a few hours.
Fiction: It’s okay to open an attachment if I know the sender…
Fact: Just because you know the sender, it doesn’t mean that the sender of the email really is who the email says it is. It is very easy for an attacker to change who it appears the email has come from, and have even been known to break into someone’s email, and then use that to send phishing emails to their contacts.
Fiction: Only some attachments are dangerous…
Fact: With the exception of text files (.txt), any attachment can be dangerous to your computer, because they can contain hidden code, or exploit a flaw within your computer.
Fiction: I’m safe from Phishing as I use a Mac
Fact: While most malware will not run on a Mac, more and more malware such as viruses are being made for the Mac, not helped by the fact that many Mac users do not run Antivirus. Also, using a Mac will not protect you from credential stealing attacks where the attacker lures you into entering your details into a website.
How does phishing work?
The aim of the attacker is to socially engineer you into acting upon the email they send you such that they can ever get hold of your personal details or logon, or so they can infect your computer with malware. Both techniques start with an email.
Step 1: Setting the trap
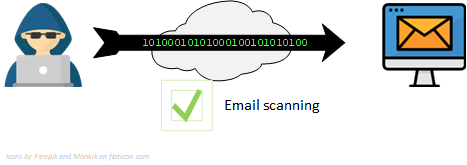
Step 1 starts with the attacker sending you an email, and crafting it in such a way that it clears your email scanning. If you are being targeted specifically (this is know as spearphishing) then the email will be highly targeted towards you, otherwise it will likely be very generic.
There are six methods which an attacker can use to socially engineer you, and they may use a combination of one or more of them:
- Fear: This involves attempting to convince you that there will be a negative outcome should you ignore the email. Examples of this include demands for unpaid bills. It is often combined with Urgency.
- Urgency: This involves attempting to convince you that you have to act quickly in order to avoid missing out. The aim is to have you rush to act without stopping to think about what you’re doing. Urgency is often combined with greed.
- Desire to be helpful: This involves attempting to convince you that you are doing the right thing (and would be a bad person if you don’t), be it helping a colleague or a family member with a problem. Examples include being asked to test a website on behalf of IT, or sending money to a stranded family member.
- Greed: This involves attempting to convince you that you’re getting something for nothing. It is often combined with Urgency and examples include Tax refund emails. Unfortunately legitimate marketing emails with special offers also exploit Greed and Urgency in an attempt to convince you to buy.
- Interesting: This involves attempting to make you click out of sheet curiosity (Clickbait). Examples include fake news articles, often about something of legitimate interest, or something pointless yet interesting such as celebrity gossip.
- Ego: This involves looking for someone who believes they won’t get caught by a phishing email, and as such, fails to protect themselves from one. An example includes a user who completed their phishing training on a Monday, proudly proclaimed that they’d done their training and wouldn’t get caught, only to be caught the very next day!
As you can see, social engineering is FUDGIE. Next time you get an email, be it spam or a real phishing email, look to see what kind of methods they’re using to socially engineer you into doing what they want.
Step 2a: Springing a malware trap
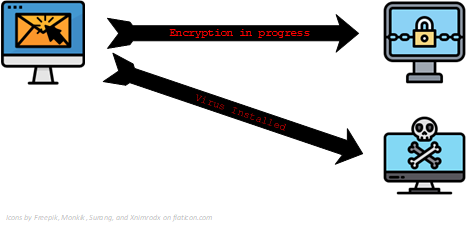
When you click on a link or open an attachment in a phishing email, the attacker will attempt to do one of two things:
- Prevent you from accessing your files by encrypting them. This is a piece of malware called Ransomware. If you have access to other computers from your own, it will then attempt to encrypt the files on those too.
- Install a virus or other malware onto your computer that can monitor what you do on your computer, often looking for you to log into online banking, where it can then steal your details; other malware can allow the attacker to take control of your computer and use it for their own purposes. This is known as a bot.
Step 2b: Springing a credential harvesting trap
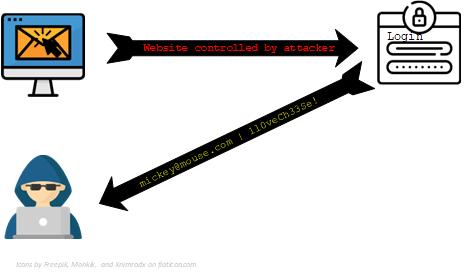
When you click the link, you will be prompted to log in, they will attempt to make the website look very similar to a genuine service such as Microsoft, Google, Apple, or PayPal. The aim is to get you to supply your username and password, which is then sent to the attacker.
They can use typo squatting to make it hard for you to tell the difference. Which website is genuine – gmail.com or gmaiI.com? The second one has a capital I instead of a lowercase L, and could in fact be a malicious website that you will struggle to spot!
Step 3: Profit
If the attacker has compromised your computer with Ransomware, once the files are encrypted, you will be given a notice of what has happened, and instructions to pay a substantial amount of money (At least many hundreds of pounds) to the attacker, usually via Bitcoin which is effectively untraceable. There is no guarantee that paying the ransom will get your files back!
Where the attacker has infected your PC with a virus, they may sell access to other people, using it as part of a “botnet”. Alternatively they may look to obtain files, usernames, and passwords which they can then use to access your email, steal valuable documents, or gain access to your bank account.
If the attacker has convinced you to log into a website and now has your details, they will then attempt to gain access to that account. Either locking you out, or installing a back door, such as an automatic forwarder on your email account that sends everything you get to them. They can then use this information to make money.
A small business case study
When you look for case studies about phishing, they are invariably about larger organisations, and often involve dealing with many phishing emails. For a small or micro business however, it only takes one email to potentially destroy a company. This case study looks at Company A, who had a near miss with a phishing email.
Late one afternoon, the secretary of a small services company which uses IT for general clerical work receives an email purporting to be from Microsoft and referring to a security issue with her Microsoft account which requires her to log in and correct. She clicks on the email which takes her to something recognisable as the Office 365 logon page. However the domain was not microsoft.com, instead it was a variant that looked like it could be Microsoft’s website, but was in fact nothing to do with them.
Having entered the username and password, the fake website now redirected her back to the genuine login page, making it look as though an error had occurred, when in fact the attacker now had her username and password. Fortunately before any damage could be done by the attacker, she called for help. A review of the email showed it to be a phishing email that was harvesting credentials.
As the user still had full access to their account at this time, they were advised to log in to the genuine Office 365 account and change their password and recovery details, and check that no configuration changes such as email forwarding had been enabled. As a last step, a malware scan was then run against their system. This scan did not reveal the presence of malware.
Additional phishing risks for small and micro businesses
While larger organisations are more likely to get caught by a phishing email, they usually have the benefit or having an IT team and tools to manage the risk this causes. When a user does fall for a phishing email, they usually have an IT person to help contain the breach quickly before any damage occurs. Should the worst happen, they usually have robust backup mechanisms that allow them to recover rapidly.
Small organisations do not have this luxury. In the case study above, had the user not been suspicious and called for help when they did, they could have lost control of their account for an extended period of time without being aware of it. While the company is not dependant on its IT for day to day operations, the loss of its IT systems would cause significant disruption to efficient working.
A further risk for small organisations is that enterprise grade security software is often priced out of reach of smaller organisations, or has such a barrier to entry that without the appropriate technical staff to implement, configure, and manage it, there would be little benefit to having it. As an example, the KnowBe4 phishing training and awareness platform starts at $17 per user per year with a minimum of 25 users ($425 or £330 per year) and then requires someone to invest time to run the testing and training.
Protecting yourself from Phishing
To properly protect yourself and your organisation from phishing, you need to consider three things together: People, Process, and Technology. Unless you address all three, you are still likely to fall victim to phishing.
People
The people controls are about getting people to act in the right way when it comes to handling email.
- Emails should never be rushed. It is very tempting to “skim through” a few emails in between other tasks. Doing this means that you may not give enough time to checking the email is safe before you act on it. Evidence from previous phishing tests showed that a significant portion of those failing their phishing testing clicked on a link within 10 seconds of opening the email!
- Always assume that an email you have received is dangerous until you have convinced yourself otherwise. If you cannot verify an email is genuine, do not act upon it – instead seek help. If it is from someone you know, email them (not by reply) to ask if the email is genuine. If it relates to something such as PayPal, go directly to the PayPal site rather than clicking on links
- Take time when reading emails. Do the following steps in order for every email:
- Check whether the email has come from someone within your organisation.
- Check that it is not spoofing your company or yourself.
- Validate who sent it, if you were not expecting an email from them use extra care.
- Inspect any links by hovering over them. Do they lead where you expect?
- Only open attachments that you were expecting to receive.
- If in doubt, ask for help.
Process
The process controls are about reducing the risk associated with handling emails.
- Minimise the use of external email where possible, especially for things such as website contacts. If you can limit distribution of your email account, you are less likely to receive phishing emails.
- Avoid conducting business entirely via email. If dealing with financial transactions online, using the phone on a known number to validate details such as account numbers stops you being subject to a man-in-the-middle attack, where a fraudster poses as the other party and provides you with false bank details to pay money to.
- Make enough time for reading emails as part of the working day. This means you may need to set aside up to an hour per day for nothing but reading. Doing this will give you time to review emails properly.
Technology
The technology controls are about preventing phishing emails from making it to your mailbox, and limiting the damage that can be done after falling for a phishing email.
- Enable 2FA on any accounts that support it. This is where you will receive a text message, or use an app on your phone to generate a code when logging in. This means that if someone got your username and password, they would not be able to use your details.
- Use a managed email service provider such as Office 365 or Google Apps for Business. These include security features including phishing protection, spoofing protection, and advanced anti-malware before the email ever gets to you. They are more expensive than standard email, but do not need extensive technical skills to set up.
- Keep your systems up to date by installing operating system and applications up to date. This will minimise the vulnerabilities that malware can exploit and generally keep your systems safer.
- Maintain regular backups of critical systems and information. This will allow you to effectively recover your business should the worst happen.
Closing thoughts
Whatever you choose to do, one of the most important things is to be vigilant to the threat of phishing, for it is likely to catch you out when you’re least paying attention.
This is also one area where it is worth seeking professional advice on training and setting up your email controls in the most secure possible manner.
